Overview
Ghidra Plugin
A more detailed look at the Ghidra Plugin can be found in this tutorial.
Targets and Gadgets
Snippets of shellcode you write with flopz that serve a distinct purpose are called gadgets by us. Because gadgets are regular python objects this allows for highly reusable code. When wanting to patch a binary with flopz, you usually define a target class that includes several methods that return gadgets for different purposes. Some example gadgets could be an init gadget that activates the necessary peripherals, or a slice gadget that has the job of jumping into different gadgets, but is also responsible for cleaning up registers and executing the original instruction in the firmware.
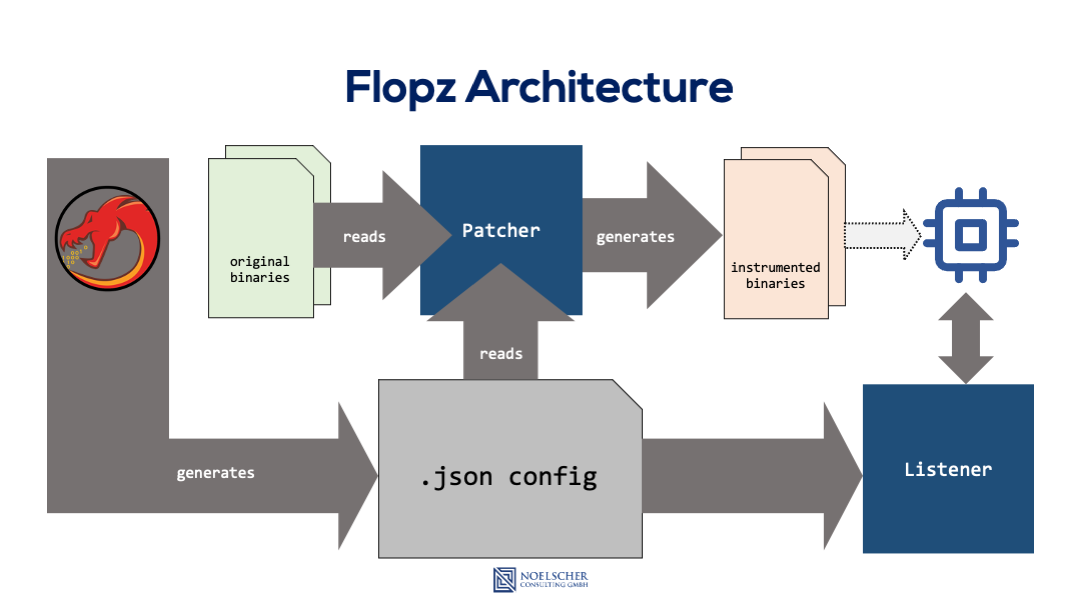
The patcher will then use the configuration created with the Ghidra Plugin and the target class to insert these gadgets into the firmware.
Read more about targets and gadgets here.
Patching The Firmware
When the configuration and the target class are prepared, the process of patching the firmware just comes down to executing the flopz_instrument.py script that comes with the flopz installation. The script needs to be fed the configuration and target class (make sure to register your target in all_targets.py), as well as the original binary and an output filename. The script will then generate the instrumented firmware by placing your shellcode into the designated locations in the original binary.
Listeners and Protocols
TODO